Boot Process: Difference between revisions
(inserted graphic) |
|||
| Line 17: | Line 17: | ||
* Asteroid-Launcher which is the desktop and wayland compositior. | * Asteroid-Launcher which is the desktop and wayland compositior. | ||
<br> | |||
[[File:Boot-process.jpg|thumb|Boot process]] | [[File:Boot-process.jpg|thumb|Boot process]] | ||
<br> | |||
= Troubleshooting the boot process = | = Troubleshooting the boot process = | ||
Revision as of 16:26, 17 June 2023
This page describes the basis of the AsteroidOS’ boot process. It’s focused on the LG G Watch but it should be similar on most other Android watches.
General description
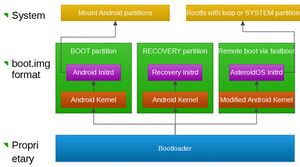
The first component loaded by the LG G Watch is the bootloader, this component is proprietary and can’t be modified, by default it is locked and only allows to boot Android, but we can access it by swiping the screen from top left to bottom right when booting up or with the adb reboot bootloader from a PC connected to a running Android or AsteroidOS instance with adb mode enabled.
This bootloader supports the fastboot protocol which is also the name of the command used on the computer to communicate with the bootloader. Fastboot allows to unlock the bootloader and then to flash partitions remotely and boot selected kernels. The bootloader can load three kernels, the one flashed on the BOOT partition, the one flashed on the RECOVERY partition and one sent via usb with the fastboot boot boot.img command. Kernels are stored in the boot.img format which is a concatenation of a kernel (sometimes with device tree) and an initramdisk. The boot.img format can be packed or unpacked with the mkbootimg and unmkbootimg tools. The AsteroidOS’s kernel is a slightly modified Android Kernel with, for example, a backported Bluetooth subsystem. The AsteroidOS’s ramdisk mostly load the init program of the rootfs which is systemd by default.
Systemd loads many components like
- Psplash which is a lightweight splashscreen software.
- Android’s init which loads the Android log daemon and servicemanager, both needed to run Asteroid-Launcher.
- DBus which is needed for inter-process communication.
- Adbd which is a daemon implementing the Android Debug Bridge protocol and which is used to get a remote shell and to push/pull files from a connected computer.
- MCE which handles the power consumption, inputs and screen…
- Patchram which loads a proprietary firmware to the broadcom bluetooth chip.
- Bluetoothd which is the BlueZ5 daemon handling bluetooth.
- Asteroid-Launcher which is the desktop and wayland compositior.
Troubleshooting the boot process
The default initramfs has a section to enable adbd on the watch before booting into the rootfs. You can enable it by appending debug-ramdisk to the boot kernel’s parameters for example with fastboot -c or fastboot --command for some versions of fastboot. For example, if you have a dory watch and the watch's fastboot file in your current directory on your computer, you can do this with this command:
<code>fastboot --cmdline debug-ramdisk boot zImage-dtb-dory.fastboot</code>
When you boot the watch, you will be able to access a command line on the ramdisk with adb shell.
Here is an example [initscript] and the [kernel configuration line] of bass.
Troubleshooting systemd
If you see the AsteroidOS logo (even for a split second), the watch is able to boot into the rootfs and launch systemd. Logs are normally stored in a tmpfs filesystem which is lost whenever the watch is rebooted. To disable the tmpfs mount, first mount the sdcard card containing the rootfs, and then the rootfs. Execute these commands as root on the watch:
<code>. /machine.conf mkdir /sdcard /rfs mount /dev/$sdcard_partition /sdcard mount -o loop /sdcard/media/0/asteroidos.ext4 /rfs </code>
You can then disable the /var/volatile tmpfs mount and enable systemd journal logging (/var/log is a symlink to /var/volatile/log):
<code>sed -i '/volatile/d' /rfs/etc/fstab mkdir /rfs/var/log/journal </code>
Once you reboot into the rootfs partition (it’ll fail again), you can hop back into the adb shell and read the journal:
<code>chroot /rfs /bin/journalctl </code>